Security researcher finds simple way to bypass Gatekeeper and allow a Mac to run malware

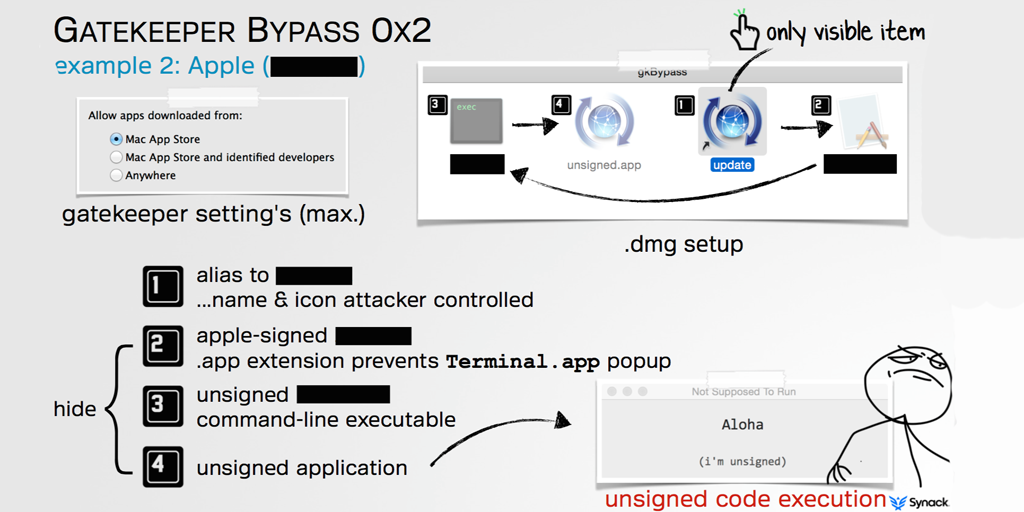
A security researcher has found an extremely simple way to bypass Gatekeeper to allow Macs to open any malicious app, even when it is set to open only apps downloaded from the Mac App Store.
Patrick Wardle, director of research at security firm Synack, told arsTechnica that once Gatekeeper okays an approved app, it pays no more attention to what that app does. The approved app can then open malicious apps – which Gatekeeper doesn’t check.
Wardle has found a widely available binary that’s already signed by Apple. Once executed, the file runs a separate app located in the same folder as the first one […] His exploit works by renaming Binary A but otherwise making no other changes to it. [He then] swaps out the legitimate Binary B with a malicious one and bundles it in the same disk image under the same file name. Binary B needs no digital certificate to run, so it can install anything the attacker wants …