Security Bite: Dangerous malware found in these commonly pirated macOS apps

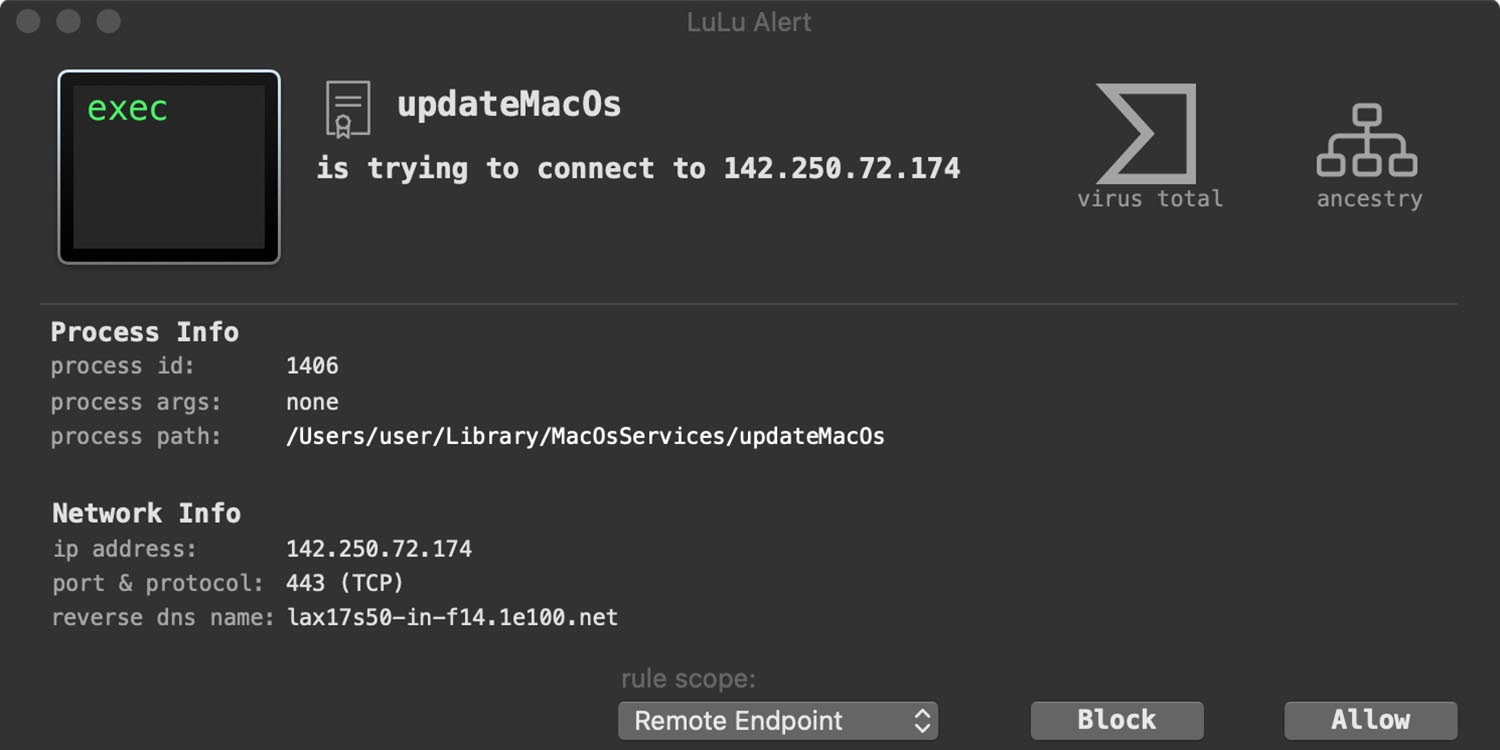
Security researchers have detected a new strain of malware hidden in some commonly pirated macOS applications. Once installed, the apps unknowingly execute trojan-like malware in the background of a user’s Mac. What happens from here is nothing good…
9to5Mac Security Bite is exclusively brought to you by Mosyle, the only Apple Unified Platform. Making Apple devices work-ready and enterprise-safe is all we do. Our unique integrated approach to management and security combines state-of-the-art Apple-specific security solutions for fully automated Hardening & Compliance, Next Generation EDR, AI-powered Zero Trust, and exclusive Privilege Management with the most powerful and modern Apple MDM on the market. The result is a totally automated Apple Unified Platform currently trusted by over 45,000 organizations to make millions of Apple devices work-ready with no effort and at an affordable cost. Request your EXTENDED TRIAL today and understand why Mosyle is everything you need to work with Apple.
Expand Expanding Close