
A new strain of Instagram phishing emails has been detected, in which attackers attempt to trick victims into forking over usernames, passwords, phone numbers, and, most notably, backup codes used to bypass two-factor authentication (2FA).
Instagram’s 2FA adds an extra layer of security to an account by requiring a second form of verification in addition to your password. This can be a one-time code sent via SMS text message, codes generated by an authentication app, or even from WhatsApp.
When configuring 2FA, Instagram gives the account a set of backup codes. These five 8-digit numbers can be used when logging into an unrecognized device or if the user can no longer verify using the two-factor authentication method (i.e., losing access to a phone). Each backup code can only be used once.
These static codes are gold for attackers, as stealing one would allow them to log into an unrecognized device by only knowing the user’s credentials, completely bypassing any 2FA. How does an attacker get all this? One way is through clever-looking phishing attacks…
New Instagram phishing campaign
Cybersecurity solutions giant Trustwave pointed out that a new phishing campaign uses emails posing as Instagram’s parent company, Meta, claiming the recipient’s account is “infringing copyrights.” The attacker also creates a sense of urgency with a message that notes an appeal must be submitted within 12 hours or else the account will be permanently deleted.
Here’s how it works…

Clicking the “Go to appeal form” link redirects the user to an initial phishing site that impersonates Meta’s actual portal for violation appeals. It’s hosted on Bio Sites, Squarespace’s quick-setup landing page platform. This, in combination with a Google notifications link, is presumably to help avoid detection from inbox spam tools and track link clicks.
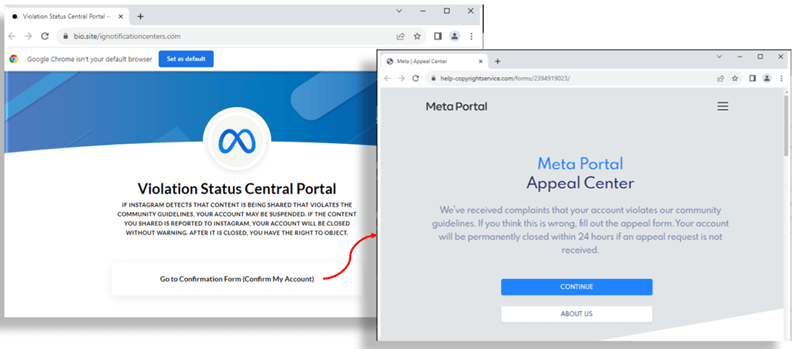
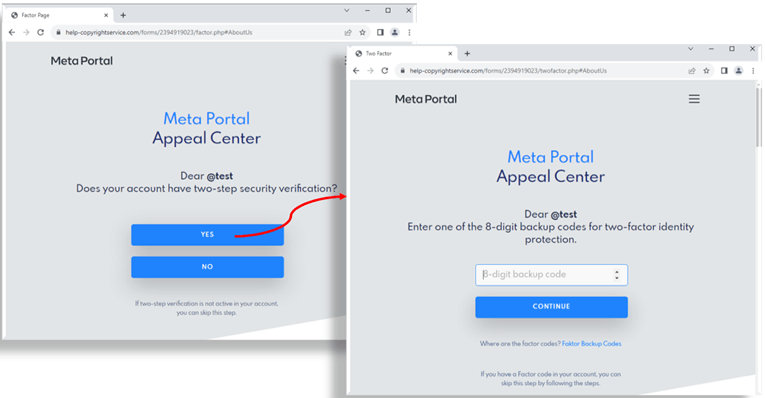
If a user proceeds by clicking the “Go to Confirmation Form (Confirm My Account),” it will redirect to another bogus Meta site, this time to collect account details. The first pieces of information requested from the user are the username and password (twice for whatever reason). After providing login credentials, the user is asked if the account has 2FA enabled.
Clicking the “YES” button asks for one of the user’s five generated Instagram backup codes. While it’s already possible to seize the account, the last screen prompts for the user’s email address and phone number.
Email continues to be the most common vector for cybercrime and phishing attacks. It’s essential to stay educated on ways to help you identify and avoid malicious emails.
The most suspicious elements here were the sender’s email (“contact-helpchannelcopyrights[.]com”), which isn’t affiliated with Meta, as well as the Google notifications URL in the appeal form button.
As a reminder, stay vigilant; do not share passwords or backup codes outside the Instagram app.
If you believe you’ve been compromised, immediately change your password and regenerate new backup codes. This can be done on Instagram by going to Settings and privacy > Accounts Center > Password and security > Two-factor authentication > [Your Instagram account] > Additional methods > Backup codes > Get new codes.
You can find Trustwave’s full report here.
Featured image via 9to5Mac/Sandeep Swarnkar.
FTC: We use income earning auto affiliate links. More.





Comments