
Back in March, we saw a piece of malware surface for macOS called MacStealer that’s able to compromise iCloud Keychain passwords, credit card information, files, and more. Now a new malware called Atomic macOS Stealer is being sold as a service to malicious parties that may be more threatening.
This year we’ve seen a report from Malwarebytes covering the state of malware on Mac as well as another study from Elastic Security Labs. In the latter, results showed just 6% of all malware impacted Macs. But even though it’s more likely to affect Windows and Linux, threat actors are actively designing malware specifically for macOS and it’s important to stay diligent.
With the MacStealer malware that we saw in March, it indeed was powerful but is likely a lower risk overall because macOS Gatekeeper should block it from being installed.
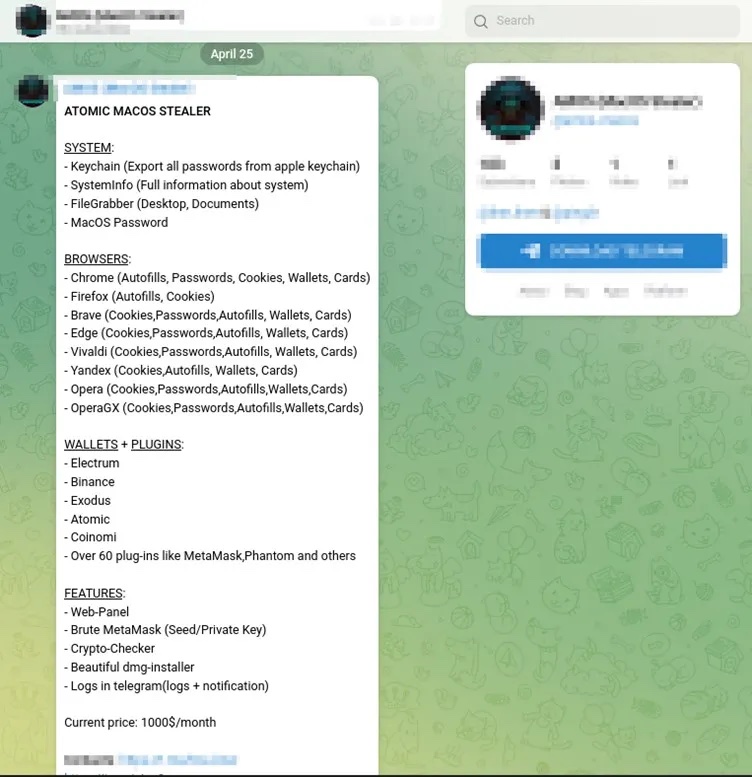
Cyble Research & Intelligence Labs (via MacRumors) recently found the new Atomic macOS Stealer (AMOS) malware as it was advertised for sale on Telegram. The threat actor marketing it is regularly updating the malware and is charging $1,000/month for it.
Notably, Cyble didn’t mention macOS Gatekeeper as offering protection for the new AMOS in its technical analysis, so it could prove more dangerous than MacStealer.
What can Atomic macOS Stealer (AMOS) do?
If installed, AMOS can compromise a long list of items including iCloud Keychain passwords; the macOS system password; cookies, passwords, and credit card details from Chrome, Firefox, Brave, Edge, Opera, and more. It can also compromise crypto wallets including Atomic, Binance, Exodus, Electrum, MetaMask, and many more.
The malicious party selling the malware as a service also includes a web panel, Brute MetaMask tool, logs in Telegram with notifications, and more to buyers.
Here is the threat actor pitching the malware on Telegram:
After the malware compromises a user’s information, it compresses the data into a ZIP file and sends it back to the malicious party through a C&C server URL.
Cyble has a detailed breakdown of how the malware works in its post here.
How to stay protected against AMOS and other malware
Cyble also shared a reminder about best practices when it comes to installing apps and broader security habits. While you probably know these, it might be helpful to remind friends and family 😁:
- Download and install software only from the official Apple App Store.
- Use a reputed antivirus and internet security software package on your system.
- Use strong passwords and enforce multi-factor authentication wherever possible.
- Enable biometric security features such as fingerprint or facial recognition for unlocking the device wherever possible.
- Be wary of opening any links received via emails delivered to you.
- Be careful while enabling any permissions.
- Keep your devices, operating systems, and applications updated.
How to check your Mac for malware
If you’re curious to do a checkup on your Mac to make sure there’s no malware or adware, Malwarebytes offers a free app (for individuals) to find and remove it.
FTC: We use income earning auto affiliate links. More.





Comments