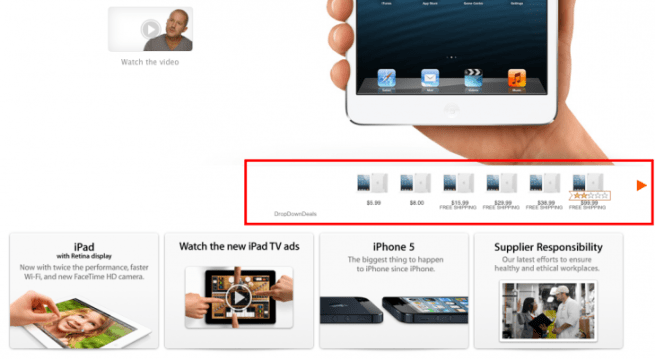
TNW reported on a new trojan discovered by Russian website Doctor Web that installs adware on Macs running all three of most popular browsers: Safari, Firefox and Chrome. Doctor Web demonstrated that the Trojan.Yontoo.1 plugin can display ads on any site by showing it in action on Apple’s own website.
Many Mac owners still believe that OS X is immune to viruses and trojans. While it’s true the platform is well protected, a large part of the relative immunity enjoyed by Mac owners has simply been down to blackhat economics: when there were many more Windows machines around than Macs, it was less worthwhile for attackers to target Macs. As the popularity of Macs has grown, however, the platform has made an increasingly attractive target.
The trojan cannot install itself and instead relies on tricking users into downloading and installing it.
This particular trojan can get onto your Mac in multiple ways. Criminals have so far used movie trailer pages that prompt users to install a browser plugin, a media player, a video quality enhancement program, or a download accelerator. In other words, the usual schemes we’ve seen on Windows.
Once installed, the plugin sends details of the webpages you visit back to a server controlled by the bad guys and uses that info to insert relevant ads. The Apple example above shows just how slickly this can be done. On a less-familiar site, a visitor could easily see the ad as part of the site.
As ever, the advice here is to only ever download known plugins from the official sites. Never accept an invitation to download anything from a website unless you know it to be a site you can trust. We’d be surprised if many 9to5Mac readers fell victim to this, but if you have family members using your Mac who might not be as careful, Intego VirusBarrier has updated its definitions to include it.
00







![osx-app-screen[1]](http://viptest.9to5mac.com/wp-content/uploads/sites/6/2014/05/osx-app-screen1.png)




 .
.