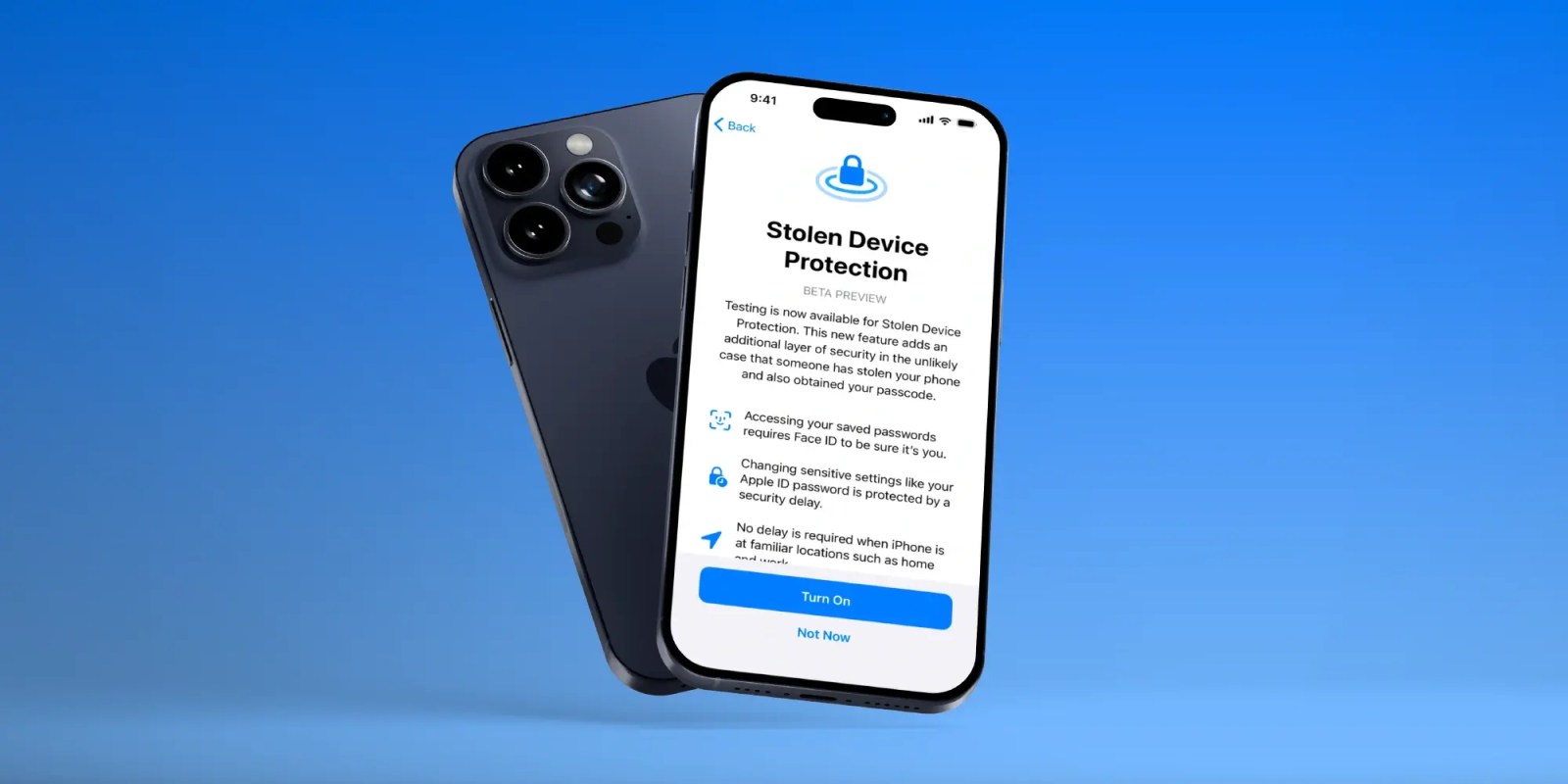
Stolen Device Protection is a great move by Apple; Activation Lock next, please

One of the key features added in the iOS 17.3 beta is Stolen Device Protection. This is a thoughtful and creative solution to balancing out the need for protecting iPhone users without stopping them do the things they want to do with their devices.
What I love about Apple’s solution here is that someone has clearly put a lot of thought into that balancing act …
Expand Expanding Close